In the dynamic world of digital assets, protecting your financial investments has never been more crucial. Cybercriminals have seized the opportunity to exploit the growing popularity of virtual currencies through sophisticated phishing techniques. The Microsoft Crypto Wallet phishing scam is a prime example of this nefarious trend, and it”s essential that we, as the crypto community, are equipped to recognize and combat these threats.
Unmasking The Microsoft Crypto Wallet Phishing Scheme
The Microsoft Crypto Wallet phishing scam revolves around a fraudulent website that impersonates the legitimate Microsoft Crypto Wallet platform. This deceptive site lures unsuspecting users with the promise of a cutting-edge cryptocurrency solution, only to deliver a malicious payload in the form of the Luca Stealer malware.
The primary objective of Luca Stealer is to covertly gather sensitive information and personal data from its victims, posing a significant threat to their financial assets and digital privacy. By gaining access to users’ private keys, login credentials, and other sensitive information, these cybercriminals can effectively drain their cryptocurrency holdings and compromise their online identities.
Recognizing The Red Flags: A Cryptonaut – S Vigilance
As a seasoned Cryptonaut, I’ve developed a keen eye for identifying the hallmarks of a phishing scam. Suspicious URLs, poor grammar, and requests for sensitive information are all red flags that should raise our vigilance. Verifying the authenticity of websites and software downloads is crucial, as is relying on reputable antivirus software and browser extensions to enhance our online security.
One of the key indicators of the Microsoft Crypto Wallet phishing site is the use of a deceptive URL that mimics the official Microsoft domain. The phishing site’s URL, “hxxps://microsoft-en.com/cryptowallet/,” is designed to appear legitimate, but a closer inspection reveals the subtle differences that set it apart from the genuine Microsoft platform. Additionally, the site’s content, which includes references to a “beta version” of the Crypto Wallet application, further reinforces the notion that this is a fraudulent attempt to capitalize on the hype surrounding Microsoft’s cryptocurrency-related developments.
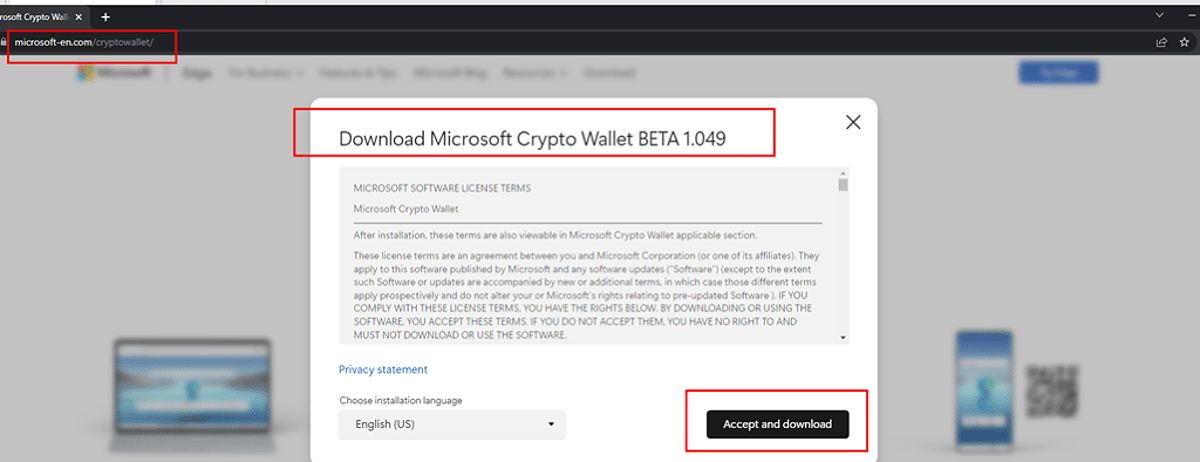 Figure 1 Phishing Site Image: A screenshot of the phishing site impersonating the Microsoft Crypto Wallet platform.
Figure 1 Phishing Site Image: A screenshot of the phishing site impersonating the Microsoft Crypto Wallet platform.
Fortifying Your Digital Fortress: Securing Cryptocurrency Wallets
As a Cryptonaut, safeguarding your cryptocurrency wallets is of paramount importance in the face of phishing threats. Implementing strong passwords, enabling two-factor authentication, and storing your private keys securely are fundamental steps to protecting your digital assets. Hardware wallets, which physically isolate your private keys, offer an additional layer of protection against phishing attacks, making them a valuable investment for cryptocurrency enthusiasts like ourselves.
In May 2024, I’ve adopted a multi-layered approach to securing my cryptocurrency holdings. I begin by creating unique, complex passwords for each of my digital wallets, and I enable two-factor authentication wherever possible. This additional security measure adds a crucial layer of protection, ensuring that even if my password is compromised, unauthorized access to my funds will be prevented.
Furthermore, I rely on hardware wallets, such as Trezor or Ledger, to significantly enhance the security of my cryptocurrency holdings. These devices physically isolate my private keys, making it exponentially more challenging for cybercriminals to gain unauthorized access to my funds. By storing my digital assets on a hardware wallet, I can rest assured that my cryptocurrency is safeguarded against phishing scams and other online threats.
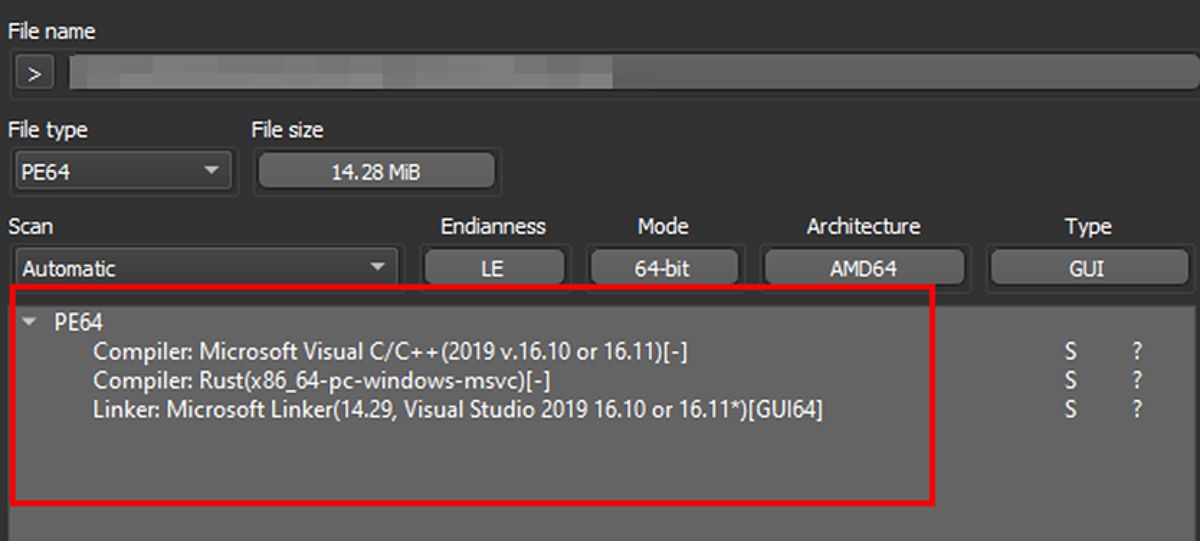 Figure 2 File Details Image: A screenshot showing the file details of the Luca Stealer malware, highlighting its malicious nature.
Figure 2 File Details Image: A screenshot showing the file details of the Luca Stealer malware, highlighting its malicious nature.
Counterattack: Reporting And Mitigating Phishing Incidents
In the unfortunate event that I’ve fallen victim to the Microsoft Crypto Wallet phishing scam, I understand the importance of taking immediate action. Reporting the incident to relevant authorities and organizations can help raise awareness and aid in the prevention of future attacks. Additionally, disconnecting my device from the internet, running a full system scan with antivirus software, and seeking the assistance of cybersecurity professionals can help mitigate the damage and protect my digital assets.
If I find that I have downloaded the Luca Stealer malware from the phishing site, I’ll act quickly to disconnect my device from the internet and prevent further data exfiltration. I’ll then run a comprehensive antivirus scan to identify and remove the malware from my system. It’s also advisable to reach out to a cybersecurity professional who can provide guidance on the appropriate steps to take, such as changing any compromised passwords and monitoring my financial accounts for any suspicious activity.
Navigating The Evolving Landscape: Staying Vigilant
As a Cryptonaut, I understand that the Microsoft Crypto Wallet phishing scam is a stark reminder of the ever-evolving threats that cryptocurrency enthusiasts face in the digital landscape. As the popularity of virtual currencies continues to grow, cybercriminals will undoubtedly devise new and sophisticated methods to target unsuspecting users. By staying informed, implementing robust security measures, and promptly reporting any suspicious activity, I can stay one step ahead of these malicious actors and safeguard my digital investments.
The open-source nature of the Luca Stealer malware, along with its development in the Rust programming language, has made it increasingly popular within cybercrime communities. As the source code is widely shared on platforms like GitHub and TOR, it’s likely that we’ll see a surge in the number of custom variants of this malware, each tailored to specific objectives and targeting a wider range of victims.
To navigate this evolving landscape, it’s crucial to remain vigilant and stay up-to-date with the latest cybersecurity trends and best practices. By regularly monitoring for new phishing scams, implementing robust security protocols, and promptly reporting any suspicious activity, I can protect my cryptocurrency holdings and minimize the risk of falling victim to these nefarious schemes.
常见问题
Q: How can I identify a legitimate Microsoft Crypto Wallet email or website? A: Verify the sender’s email address and check for any suspicious URLs or grammatical errors. Legitimate Microsoft communications will come from official Microsoft domains.
Q: What should I do if I have downloaded the Luca Stealer malware? A: Disconnect your computer from the internet, run a full system scan with antivirus software, and contact a cybersecurity professional for assistance.
Q: How can I protect my cryptocurrency from future phishing scams? A: Use strong passwords, enable two-factor authentication, store private keys securely, and be vigilant about identifying and avoiding phishing attempts.
结论
As a Cryptonaut, I understand the importance of proactive cybersecurity measures in the world of cryptocurrency. By understanding the tactics used by these malicious actors, implementing robust security protocols, and promptly reporting any suspicious activity, I can safeguard my digital assets and minimize the risk of falling victim to these nefarious schemes.
The Microsoft Crypto Wallet phishing scam serves as a stark reminder of the evolving threats we face in the dynamic cryptocurrency landscape. However, with a keen eye for detecting red flags, a multi-layered approach to securing our wallets, and a steadfast commitment to staying informed and vigilant, we can fortify our digital fortresses and protect our cryptocurrency investments from the grasp of cybercriminals.
Remain vigilant, stay informed, and let your digital fortress be the impenetrable shield that safeguards your cryptocurrency holdings. Together, as a united Cryptonaut community, we can navigate the ever-changing landscape and emerge victorious in the face of these nefarious phishing schemes.















 比特币
比特币  以太坊
以太坊  拴
拴  XRP
XRP  索拉纳
索拉纳  USDC
USDC  狗狗币
狗狗币  卡达诺
卡达诺  TRON
TRON